In case you haven’t heard, on May 25, 2021, VMware published a particularly dangerous vulnerability.
Typically, they will rate these with a number between 1 and 10 to identify the level of severity and importance, and this particular vulnerability (which also warranted a blog post) scored a 9.8, one of the highest scores available.
The short version is that due to a security flaw in the vSphere Client (webpage), a malicious actor with access to port 443 on the vCenter may exploit commands with unrestricted privileges on the underlying OS that hosts the vCenter Server.
Patch Your VMware Environment to Protect It
To protect against these active attacks, we’ll want to ensure your vCenter server versions are patched at least up to:
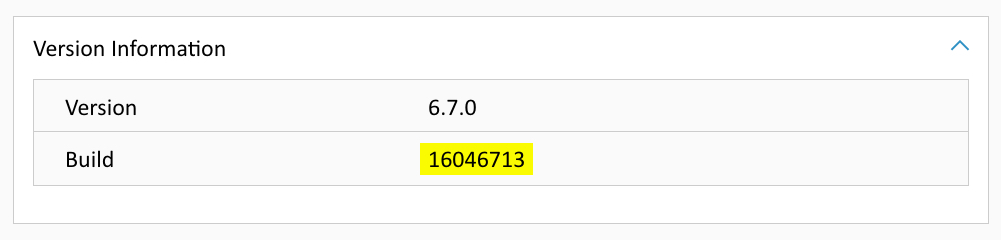
- vCenter Server 7.0 U2b (Build 17958471)
- vCenter Server 6.7 Update 3n (Build 18010531)
- vCenter Server 6.5 Update 3p (Build 17994927)
Quickly find your version and build number by navigating to the vCenter top level object in the vCenter UI, clicking on the summary tab, then scrolling down to version information. (See screenshot below.)
If you’re unable to update your vCenter Server to a version with a patched security issue, you can follow the workaround to disable several of the plugins (click here).
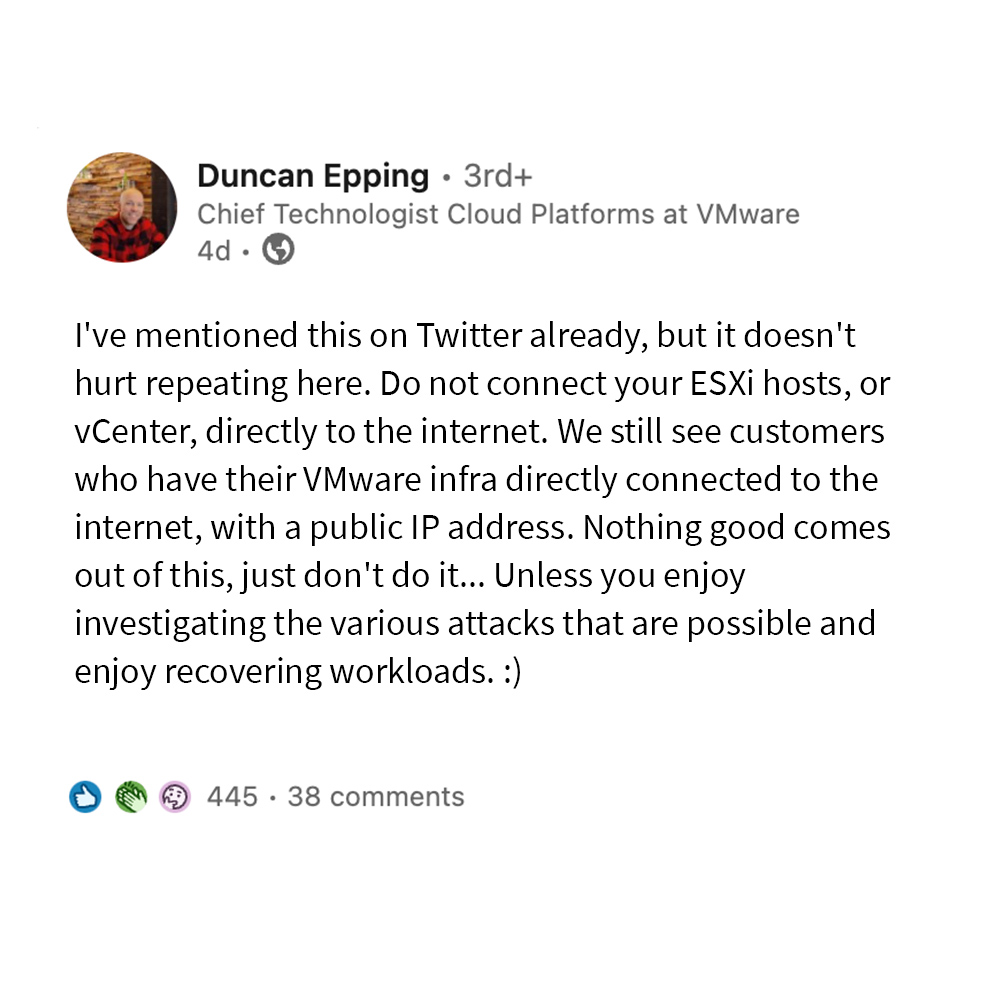
As always, there are many best practices for keeping your VMware environment safe. In regard to this particular vulnerability, you don’t want to expose your vCenter or ESXi hosts directly to the public internet. Even the famous Duncan Epping at VMware sounded off on LinkedIn (above), citing that connecting your vCenter or ESXi hosts directly to the public internet is just a bad idea.
As a fellow VCDX, I completely agree with him.
7 Ways to Harden Your VMware Environment
If you are looking for additional ways of hardening your environment, you can always visit the VMware Security Hardening Guides page, and go to the Security Configuration Guide. Some of the frequent findings you’ll see in most of these guides and come up often on Advizex health check services are:
1. Keep all VMware instances patched whenever possible
2. Use RBAC roles within vCenter to follow the principle of least privilege
3. Save log files on a separate server such as a syslog or SIEM system
4. Disable SSH on ESXi servers until required or filter access to it
5. Use privileged accounts for administration and regular accounts for non-administrative needs
6. Ensure your vCenter is leveraging file-based backup and recovery, if available
7. Ensure ESXi VMkernel management network interfaces are isolated whenever possible.
